Docker recently introduced a new service – Docker Hardened Images (DHI). These are container images that are secure by default, built specifically for modern production environments.
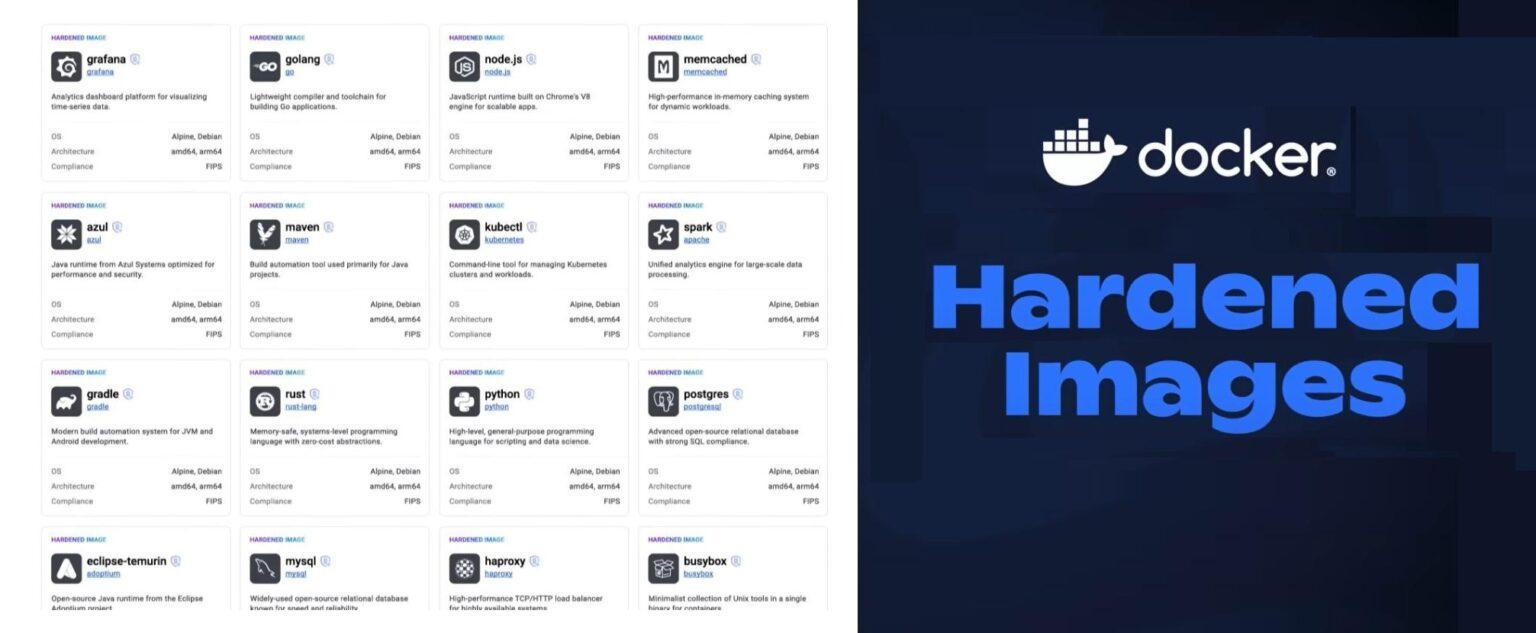
These images are much more than just slim or minimal. Docker Hardened Images start with a dramatically reduced attack surface, up to 95% smaller, to limit exposure from the very beginning.
Docker maintains the images and updates them continuously to ensure near-zero known vulnerabilities (CVEs).
The images support common distributions like Alpine and Debian, so teams can integrate them without needing new tools or compromising compatibility.
Additionally, they are designed to work seamlessly with the tools already in use. Docker has partnered with a variety of leading security and DevOps platforms, including Microsoft, NGINX, Sonatype, GitLab, Wiz, Grype, Neo4j, JFrog, Sysdig, and Cloudsmith, to ensure smooth integration with scanning tools, Container Registries, and CI/CD pipelines.
Watch a brief overview of Docker Hardened Images (1 min.):
What do Docker Hardened Images provide?
Docker Hardened Images are not just stripped-down versions of existing containers –
they are built from the ground up with security, efficiency, and real-world usability in mind.
They are designed to meet development and DevOps teams where they work. They provide value in three essential areas:
1. Seamless Migration
First, they integrate seamlessly into existing workflows.
Unlike other minimal or “secure” images that force teams to change operating systems (OS),
rewrite Dockerfiles, or abandon their tools,
DHI supports distributions developers already use, including familiar versions of Debian and Alpine.
In fact, upgrading to DHI can be simple.
Switching to a hardened image is as simple as updating a single line in the Dockerfile.
2. Flexible Customization
Second, the hardened images strike the right balance between security and flexibility. Security should not come at the expense of usability.
DHI supports customizations that teams rely on, including certificates, packages, scripts, and configuration files, without compromising the hardened foundation. Users get the level of security they need with the flexibility to adapt images to their environment.
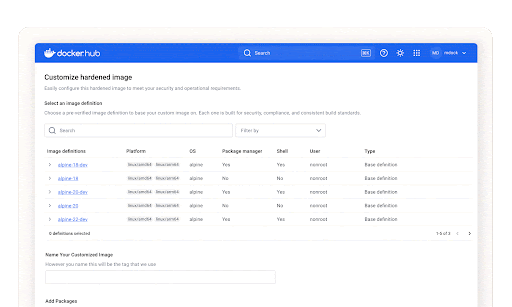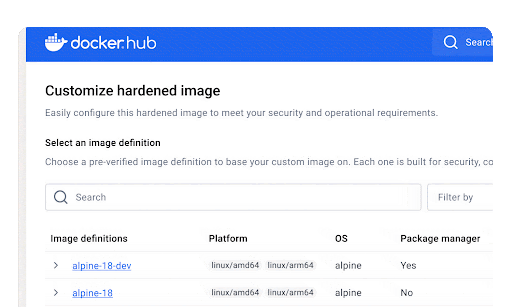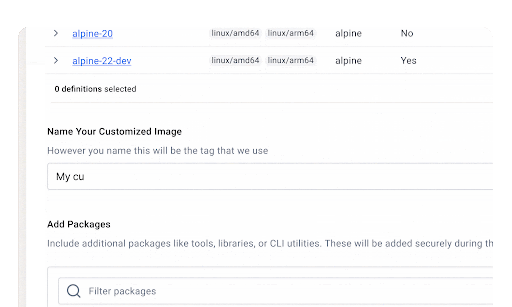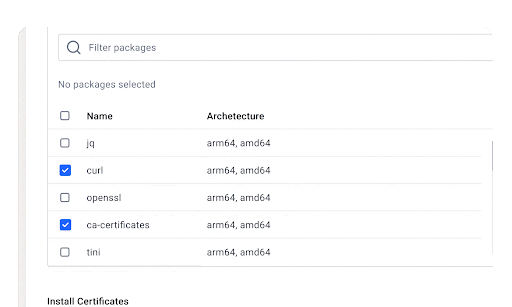
Under the hood, Docker Hardened Images follow a “distroless” philosophy, removing unnecessary components like shells, package managers, and debug tools that typically introduce risk.
While these additions may be useful during development, they significantly expand the attack surface in production, slow down boot times, and complicate security management.
By including only the essential runtime dependencies needed to run your application, DHI provides leaner, faster containers that are easier to secure and maintain. This focused, minimal design leads to an up to 95% reduction in the attack surface, giving teams a dramatically stronger security posture from day one.
3. Automatic Security Updates and Rapid CVE Response
Finally, security and version updates are continuous and automatic. Docker monitors external sources, OS packages, and CVEs across all dependencies.
When updates are released, DHI images are rebuilt, undergo comprehensive testing, and are published with new attestations – ensuring integrity and compliance with standards within our build system, which is compliant with SLSA Build Level 3. The result: you always run the most secure and verified version – with no manual intervention required.
Most importantly, when essential components are built directly from the source, it allows for faster delivery of critical security updates and immediate remediation of vulnerabilities.
Docker commits to an SLA to fix critical and high-severity CVEs within 7 days – faster than industry-standard response times – and backs it all with an enterprise-level SLA for additional peace of mind.
4. FedRAMP-ready variants (FIPS-enabled, STIG-ready)
If you are working to achieve FedRAMP certification, complying with strict security standards like FIPS and STIG is not optional – it is mission-critical.
But manually hardening container images is time-consuming, requires endless maintenance, and is prone to human error.
Now, Docker Hardened Images are offered with FedRAMP-ready variants, designed to meet US federal security requirements “out of the box”. These images are FIPS-enabled for strong, validated cryptographic enforcement, STIG-ready with secure default settings integrated, and are provided with signed Software Bills of Materials (SBOMs) and attestations for full auditability.
Short demo here (1 min.):
In summary:
Docker Hardened Images enable the use of images that are secure from the start, save significant time in their preparation, reduce image download and load times (because they are reduced to the minimum possible size), and prevent significant exposure to vulnerabilities in production and at runtim.
For more details regarding purchase and to receive a trial, you can contact us.
Our company, ALM Toolbox, is the official representative of Docker in Israel (at the highest “Preferred Partner” level).
We offer support on the subject, assistance in choosing the appropriate licensing, sales of Docker licensing, as well as help with hardening containers and CI/CD pipelines, and planning DevOps, DevSecOps, and AppSec processes.
For more details, contact us by email at docker@almtoolbox.com
or call 866-503-1471 (USA & Canada) / +31 85 064 4633
Related Links



